腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Industry News ] Proofpoint 研究员发现 Turla APT 团伙对其 KopiLuwak JavaScript 后门改进后用于以 G20 为主题的鱼叉式攻击: https://www.proofpoint.com/us/threat-insight/post/turla-apt-actor-refreshes-kopiluwak-javascript-backdoor-use-g20-themed-attack
-

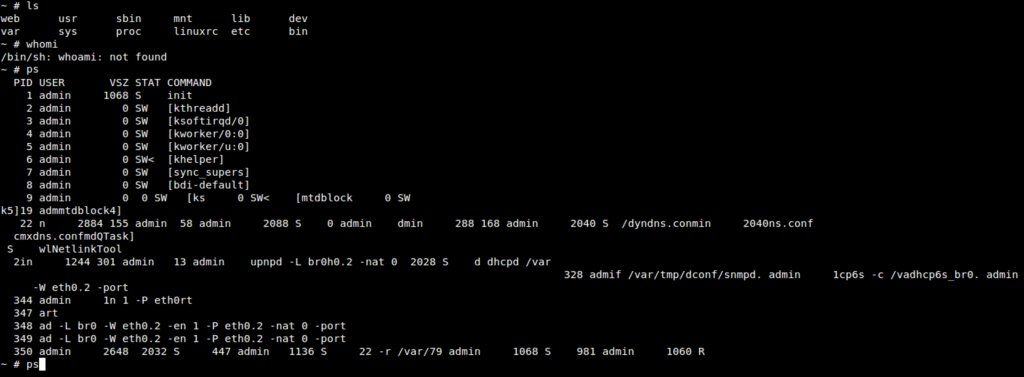
[ IoTDevice ] Gaining root via UART : http://konukoii.com/blog/2018/02/16/5-min-tutorial-root-via-uart/
-

[ MachineLearning ] 人工智能是如何阻止 Emotet 爆发的: https://cloudblogs.microsoft.com/microsoftsecure/2018/02/14/how-artificial-intelligence-stopped-an-emotet-outbreak/
-

[ Malware ] McAfee 团队最近发现一款勒索软件在暗网(Dark Web)中可被免费使用 : https://securingtomorrow.mcafee.com/mcafee-labs/free-ransomware-available-dark-web/
-

[ Others ] GCHQ Computer Network Exploitation: https://www.documentcloud.org/documents/4380643-GCHQ-Computer-Network-Exploitation-presentation.html#document/p1
-

[ Tools ] modjoda - Android 上的 Java 反序列化工具: https://github.com/SECFORCE/sparta
-

[ Tools ] MSDAT - Microsoft SQL DB 攻击工具: https://github.com/quentinhardy/msdat
-

[ Tools ] IntruderPayloads - Burpsuite Intruder 常用的 Payloads 收集: https://github.com/1N3/IntruderPayloads
-
-

[ Tools ] Privileged Access Workstation (PAW) - 企业管理员安全管理设备、防御密码窃取、防御摆渡攻击的一套工具集: https://github.com/unassassinable/PAW
-

[ Tools ] whapa - whatsapp database parser: https://github.com/B16f00t/whapa
-

[ Web Security ] 通过 CSS 窃取数据: https://www.mike-gualtieri.com/posts/stealing-data-with-css-attack-and-defense
-

[ Windows ] 使用 MSIEX 绕过 Windows 应用程序白名单: https://homjxi0e.wordpress.com/2018/02/17/whitelisting-bypassing-using-msiex/