腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

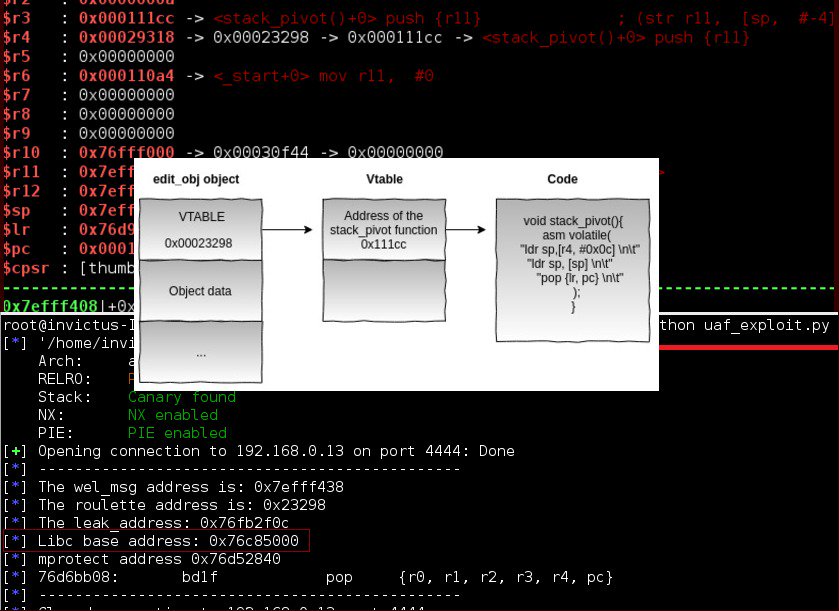
[ Firmware ] ARM exploitation for IoT - 基于增强版 GDB 调试工具 GEF 调试 ARM Exploit: https://quequero.org/2017/11/arm-exploitation-iot-episode-3/
-

[ Industry News ] US-CERT 提醒大家要警惕 IEEE P1735 最近修复的几个加密漏洞: https://threatpost.com/us-cert-warns-of-crypto-bugs-in-ieee-standard/128784/
-

[ Industry News ] 以太区块链平台(Ethereum )的 Bug 造成 2.8 亿美金被冻结: https://blog.comae.io/the-280m-ethereums-bug-f28e5de43513
-

[ Linux ] 通过 syzkaller Fuzz 出来的 Linux 内核 USB 子系统的 11 个漏洞(CVE-2017-16525/CVE-2017-16526/CVE-2017-16527/.../CVE-2017-16538): http://www.openwall.com/lists/oss-security/2017/11/06/8 https://github.com/google/syzkaller/blob/master/docs/linux/found_bugs_usb.md
-

[ Linux ] Linux 内核中的 Double Fetch 漏洞研究,来自 USENIX 2017 会议的 Paper: https://www.usenix.org/system/files/conference/usenixsecurity17/sec17-wang.pdf
-

[ Linux ] 对 Linux 内核 Waitid 系统调用本地提权漏洞(CVE-2017-5123)的分析与利用: https://reverse.put.as/2017/11/07/exploiting-cve-2017-5123/
-

[ Linux ] Linux 内核 FILE 数据结构的剖析以及基于 FILE 的二进制利用技术: https://www.slideshare.net/AngelBoy1/play-with-file-structure-yet-another-binary-exploit-technique
-

[ Malware ] 美国马里兰大学的研究员对恶意软件滥用有效证书签名的问题的研究: https://threatpost.com/assessing-weaknesses-in-public-key-infrastructure/128793/
-

[ MalwareAnalysis ] 恶意软件分析平台 FAME,来自 VirusTotal VB2017 会议的公开的一个分析系统: https://www.virusbulletin.com/uploads/pdf/magazine/2017/201710-FAME.pdf https://certsocietegenerale.github.io/fame/ https://github.com/certsocietegenerale/fame
-

[ MalwareAnalysis ] REDBALDKNIGHT / BRONZE BULTER 间谍团伙近期动态分析: http://blog.trendmicro.com/trendlabs-security-intelligence/redbaldknightbronze-bulters-daserf-backdoor-now-using-steganography/
-

[ Others ] Google 的 Certificate Transparency 计划可以帮助用户实时监控证书可信任性。有研究员基于它开发了一个监控日志服务 - CertStream,再配合写个简单的脚本,就可以监控可疑域名的证书信息变动提醒了: https://blog.0day.rocks/catching-phishing-using-certstream-97177f0d499a https://medium.com/cali-dog-security/introducing-certstream-3fc13bb98067 https://github.com/x0rz/phishing_catcher/blob/master/catch_phishing.py
-
-
-

[ Popular Software ] Ametys CMS 未授权密码重置漏洞披露: https://blogs.securiteam.com/index.php/archives/3517
-

[ Tools ] PCILeech FPGA - 与 PCILeech DMA 攻击套件相关的 HDL 代码: https://github.com/ufrisk/pcileech-fpga
-

[ Vulnerability ] 亚马逊 AWS 多因素认证安全策略中的潜在安全隐患: https://duo.com/blog/potential-gaps-in-suggested-amazon-web-services-security-policies-for-mfa
-

[ Windows ] Bypassing Modern Process Hollowing Detections (via Hotswapping Maps): http://riscy.business/2017/11/bypassing-modern-process-hollowing-detection/
-

[ Windows ] Windows 10 最新版将 EMET 集成到 Windows Defender 后,有一个新特性叫做 ASR(Attack Surface Reduction),ASR 的其中一个规则是阻断 VBScript/JS 脚本执行下载的可执行代码。这篇 Blog 详细分析这个规则: https://www.darkoperator.com/blog/2017/11/6/windows-defender-exploit-guard-asr-vbscriptjs-rule
-
-
-

[ Compiler ] 之前推送过一篇 Paper《Compiler-Agnostic Function Detection in Binaries》,在二进制文件中检测函数的方法。现在作者要将这个技术移植到 Binary Ninja 二进制分析框架中了: https://www.vusec.net/2017/11/nucleus-picked-binary-ninja/
-
-

[ MalwareAnalysis ] 腾讯安全反病毒实验室:Nitol僵尸网络家族变种借“快猴网”套“肉鸡: https://weibo.com/ttarticle/p/show?id=2309404171461119097851
-
-
-
-