
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Browser ] Mozilla to distrust WoSign and StartCom https://docs.google.com/document/d/1C6BlmbeQfn4a9zydVi2UvjBGv6szuSB4sMYUcVrR8vQ/preview
"Mozilla 将不再信任 WoSign 和 StartCom 颁发的新证书: https://t.co/ug8Th1ljfA"
-

[ Conference ] Derbycon 2016 Videos: http://www.irongeek.com/i.php?page=videos/derbycon6/mainlist
"Derbycon 2016 会议的所有视频︰ https://t.co/x85yaxTZFf"
-

[ Detect ] Introducing DeepBlue CLI : A PowerShell module for Hunt Teaming via Windows Event Logs : https://drive.google.com/file/d/0ByeHgv6rpa3gNU4wLVZKNjd4cTA/edit
" DeepBlue CLI - 基于 Windows 事件日志检测威胁的工具,PowerShell 编写: https://t.co/ggk03K7nsL"
-

[ Fuzzing ] Project Springfield : Fuzz your code before hackers do https://www.microsoft.com/en-us/springfield/#examples
" 微软推出 Project Springfield Fuzzing 测试服务: https://t.co/YEPZud9rgA"
-

[ iOS ] My slides "Malware wellbeing on iOS devices" https://dsec.ru/upload/medialibrary/29f/29f57cef406125e9169da733e1aaf83f.pdf
" iOS 的安全特性和恶意软件总结,来自 DigitalSecurity 的 PPT: https://t.co/aXuYDBwa51"
-

[ macOS ] New #Unit42 research on Komplex: an OS X Trojan with links to #Sofacy group http://bit.ly/2d73xem
" 一款新的 OS X 木马 Komplex,与 Sofacy 组织有关,来自 Palo Alto: https://t.co/yW1XSSjSgU "
-

[ Others ] New blog post: Diving into EMET https://www.insinuator.net/2016/09/diving-into-emet/
" EMET 深度分析,含几乎所有的 EMET 历史文章的列表: https://t.co/GnvcG3ls7P"
-

[ Others ] Simple Guide to Finding a JavaScript Memory Leak in Node.js : https://www.alexkras.com/simple-guide-to-finding-a-javascript-memory-leak-in-node-js
"在 Node.js 中找 JavaScript 内存泄漏的 Bug︰ https://t.co/AJzYpvECQr"
-

[ Others ] If you patched OpenSSL last week, do it again: https://www.openssl.org/news/secadv/20160926.txt :)
" 上周的 OpenSSL CVE-2016-6307 漏洞的补丁引入了一个新的 UAF 漏洞,如果你上周打了补丁,那就再打一次吧︰ https://t.co/e2Bi6Mw8JP "
-

[ Pentest ] Here are the slides from our talk on Mettle at @ derbycon, now with diagrams: http://www.slideshare.net/BrentCook2/static-pie-how-and-why-metasploits-new-posix-payload-mettle
" Metasploit 的新 POSIX Payload: Mettle,来自 DerbyCon 会议的演讲: https://t.co/QJvsK1jyxc"
-

[ Popular Software ] MSI ntiolib.sys/winio.sys local privilege escalation http://blog.rewolf.pl/blog/?p=1630
"MSI(微星)驱动 ntiolib.sys/winio.sys 本地提权漏洞: https://t.co/MoyPKYb7CQ"
-

[ Tools ] Introducing MailSniper : A Tool For Searching Every User’s Email for Sensitive Data : http://www.blackhillsinfosec.com/?p=5296
" MailSniper - 从邮件中搜索敏感数据的工具︰ https://t.co/lfWJDdRhgb"
-

[ Tools ] from markdown to slides https://yhatt.github.io/marp/ #porn
" 从 Markdown 转成幻灯片的工具: https://t.co/fzs0KGFkOY "
-

[ Windows ] A new version of my TpmInit UAC bypass tool (using PEB Masquerading) is available at https://github.com/Cn33liz/TpmInitUACBypass and https://t.co/GuiltQjE7j
" TpmInit UAC Bypass Tools: https://github.com/Cn33liz/TpmInitUACBypass https://github.com/Cn33liz/TpmInitUACAnniversaryBypass "
-

[ Windows ] New blog post about @breenmachine's Derby talk - Privilege Escalation from Service Accounts to SYSTEM in Windows https://t.co/ta0RTTaEMs
" 昨天推送了一个 Windows 服务帐户提权至 SYSTEM 的工具 RottenPotato,作者昨天写了一篇 Blog 谈技术细节: https://t.co/ta0RTTaEMs "
-

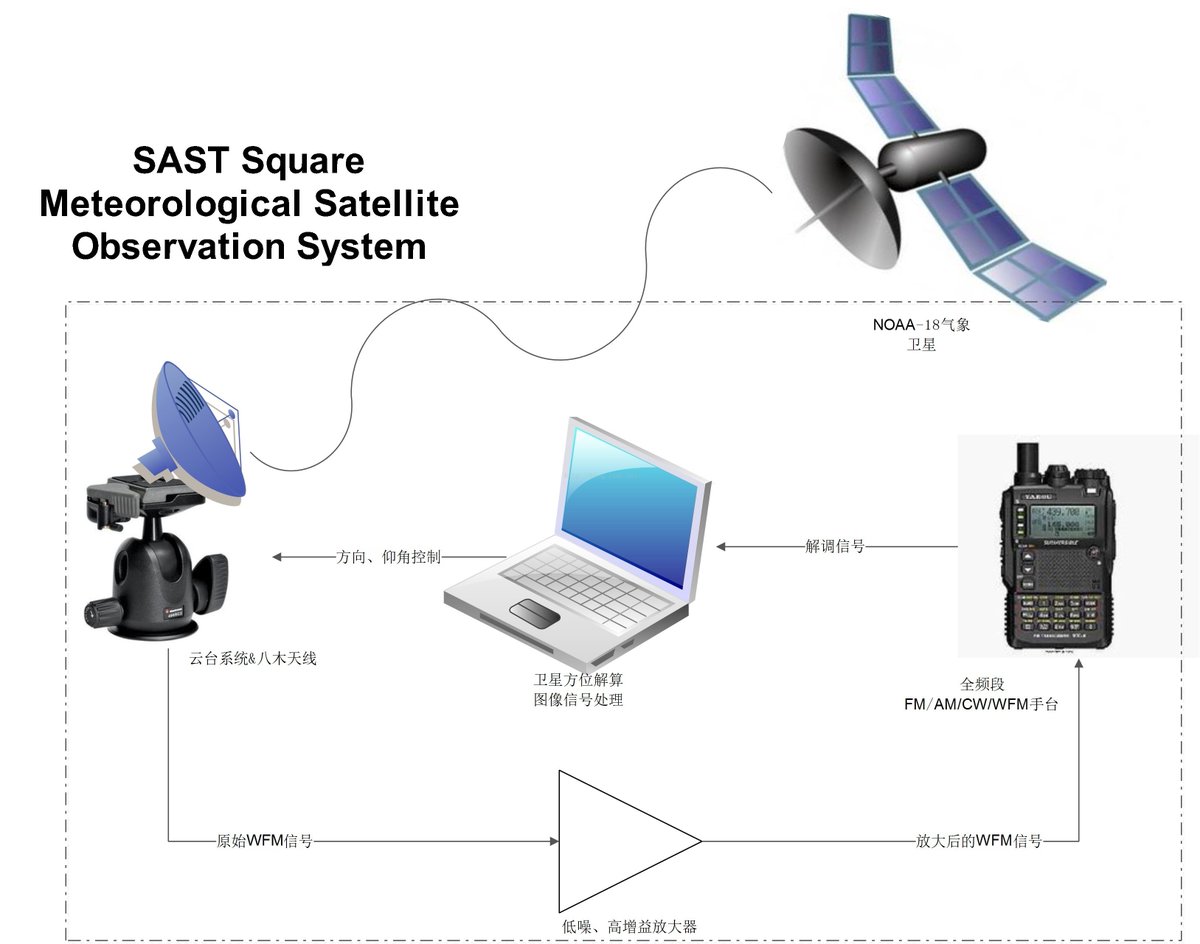
[ WirelessSecurity ] 气象卫星云图观测接收 MeteorologicalSatellite Observation And Receiving #SDR #HackRF #BladeRF http://blog.csdn.net/xdyegong/article/details/49851507 https://t.co/CnHdPzJlFn
" 气象卫星云图观测接收,来自 CSDN: https://t.co/LiPMciZ8UG "
-
[ Browser ] Safari UXSS 漏洞分析(CVE-2016-4758),来自 Holic (知道创宇 404 安全实验室)翻译自 Masato Kinugawa 的一篇文章: http://paper.seebug.org/53/
-
[ Browser ] Chromium 扩展(Extension)的Content Script加载过程分析: http://blog.csdn.net/luoshengyang/article/details/52465364
-
[ Crypto ] 解读 OpenSSL CVE-2016-6304漏洞: http://mp.weixin.qq.com/s?__biz=MzA3Mzk1MDk1NA==&mid=2651903473&idx=1&sn=3e937bb37a8c15ded2d6bda241c8cbe9&mpshare=1&scene=1&srcid=0923GXqe0CGNJJchYpqijzqS
 Xuanwu Spider via Seebug
Xuanwu Spider via Seebug