
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Android Banking Trojan First to Gain Root Privileges https://threatpost.com/android-banking-trojan-first-to-gain-root-privileges/120707/
" 利用 Exploit 获取 Root 权限的 Android 银行木马: https://t.co/EABSFerZeJ 来自卡巴斯基的技术分析: https://securelist.com/blog/mobile/76101/the-banker-that-can-steal-anything/ "
-

[ Android ] Great Android Security article. @ AndroidTamer thanks for sharing! https://androidtamer.com/learn_android_security
" Learn Android Security,关于 Android 安全的文章集锦: https://t.co/l9Lei3WA1r"
-

[ Browser ] Browser Bug Searcher https://browser-issue-tracker-search.appspot.com/ ? a thing to ? for ? across all major browser vendor issue trackers. https://t.co/0jBV09Pw42
" Browser Bug Searcher: https://browser-issue-tracker-search.appspot.com "
-

[ Browser ] Apple Safari 10 (multiple remote code execution vulns) https://support.apple.com/en-us/HT207157
"苹果公开了 Safari 10 的漏洞公告,其中包括 WebKit 组件的多个漏洞: https://t.co/TfPyqnnM4R"
-

[ Crypto ] Slides and videos from #whibox2016 are now available! https://www.cryptoexperts.com/whibox2016/ https://t.co/Whj80wMmUE
" 以加密为主题的 WhibOx 2016 会议的 PPT 可以下载了: https://t.co/sfSG7yU59U "
-

[ Crypto ] Ruby OpenSSL + GCM Nonce Reuse Bug http://www.openwall.com/lists/oss-security/2016/09/19/9
"Ruby OpenSSL + GCM 随机数重用 Bug: https://t.co/rEwlh3nKsZ"
-

[ Hardware ] Remote Attack Tesla Motors: Video demonstration by Keen Security http://keenlab.tencent.com/en/2016/09/19/Keen-Security-Lab-of-Tencent-Car-Hacking-Research-Remote-Attack-to-Tesla-Cars/
" 腾讯科恩实验室最新研究成果:对特斯拉的无物理接触远程攻击(含视频演示): http://keenlab.tencent.com/zh/2016/09/19/Keen-Security-Lab-of-Tencent-Car-Hacking-Research-Remote-Attack-to-Tesla-Cars/ ; 视频链接地址: http://v.qq.com/x/page/y0329yuyczc.html 关于特斯拉的破解, Lookout 的研究员曾经公开过一份很详细的技术文档: https://blog.lookout.com/blog/2015/08/07/hacking-a-tesla/ 国内研究员 RAyH4c 也写过一篇文章谈特斯拉的破解: http://m.leiphone.com/news/201509/kt568ZkCEZNThbgZ.html "
-

[ Linux ] "Anatomy of a Real Linux Intrusion Part II: OpenSSH trojanized toolkit" http://blog.angelalonso.es/2016/09/anatomy-of-real-linux-intrusion-part-ii.html (by @ Angelill0, based on MiTM SSH honeypot)
" 一次真实的 Linux 入侵过程分析 - 被木马化的 OpenSSH Part 2: https://t.co/b6n33ybv9s"
-

[ Malware ] iSpy Keylogger Analysis | @ zscaler https://www.zscaler.com/blogs/research/ispy-keylogger
" iSpy Keylogger 分析,来自 Zscaler Blog: https://t.co/tWyHOasJBA"
-

[ Mobile ] Threat Analysis of Malicious Applications on Mobile Operating Systems : https://www.ernw.de/download/newsletter/ERNW_Newsletter_55_Threat_Analysis_v1.0_signed.pdf (pdf) cc @ Enno_Insinuator
"手机操作系统上的恶意应用威胁研究,来自 ERNW 的 Paper︰ https://t.co/UaEb9plZCR "
-

[ Mobile ] Mobile Security News Update September 2016 https://www.mulliner.org/blog/blosxom.cgi/security/mobile_security_news_update_sep2016.html <-- Very Android Heavy
" Collin R. Mulliner 总结的 9 月份的移动安全热点: https://t.co/MdOLylrvw2 "
-

[ Network ] Link to my @ 44con slides on VLAN Hopping http://info-assure.co.uk/public_downloads/not-only-frogs-can-hop.pdf and the Frogger2 tool https://github.com/commonexploits/vlan-hopping
" VLAN Hopping(跳跃攻击): https://t.co/oOISSNinE5 VLAN Hopping Frogger2 攻击脚本: https://t.co/1o4lpxWmkq"
-

[ Network ] A peek behind the great firewall of Russia #blogpost https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2016/september/a-peek-behind-the-great-firewall-of-russia/
" 俄罗斯的国家防火墙简单介绍: https://t.co/q8IdlyU9ha "
-

[ Others ] North Korea accidentally leaks DNS for .kp: only 28 domains https://github.com/mandatoryprogrammer/NorthKoreaDNSLeak
" 朝鲜一不小心泄漏了 DNS .kp 域信息: https://t.co/yUyy4mpDfX"
-

[ Others ] When students are sent to modify a modern JIT engine: http://www.cs.cmu.edu/~auc/CompilersReport.pdf
" 一篇关于 JIT 引擎的 Paper《Just-in-time Parameter Specialization》︰ https://t.co/SBSWFypMQH"
-

[ Others ] Oh noes!!!11! They put WebKit into Emacs: https://www.reddit.com/r/emacs/comments/4srze9/watching_youtube_inside_emacs_25/
" Emacs 代码编辑器 25 版本将集成 WebKit,这样就可以在 Emacs 中看 YouTube 视频了: https://t.co/7NXg1j640q"
-

[ Others ] RCE exploit found in Metasploit itself, delighting irony lovers everywhere : https://github.com/justinsteven/advisories/blob/master/2016_metasploit_rce_static_key_deserialization.md
" Metasploit 4.12 版本自身的 RCE 漏洞,与反序列化有关︰ https://t.co/aanHPGNxIT"
-

[ Popular Software ] Hacking WordPress Sites on Shared Servers https://blog.sucuri.net/2016/09/hacking-wordpress-sites-shared-servers.html
" Hacking 共享服务器上的 WordPress 站点: https://t.co/7TBl9puitF "
-

[ SecurityProduct ] RogueKiller, Inside WMI Scanner http://www.adlice.com/roguekiller-inside-wmi-scanner/
"反病毒软件 RogueKiller 增加了一个新功能 WMI Scanner: https://t.co/zbmuzi2oWK"
-

[ SecurityProduct ] More Symantec and Norton remote code execution vulnerabilities fixed today, full advisory is here. https://www.symantec.com/security_response/securityupdates/detail.jsp?fid=security_advisory&pvid=security_advisory&year=&suid=20160919_00
" 赛门铁克和诺顿安全软件近几天修复了两个远程代码执行漏洞,官方公告: https://t.co/BLnaUQuI9l"
-

[ Tools ] A quick slides on why we created Keypatch assembler for IDA, and how this tool is designed & implemented: https://t.co/ikBXn9kKmD
" IDA Pro 的汇编器插件 Keypatch,来自官方的一篇 PPT︰ https://t.co/ikBXn9kKmD"
-

[ Windows ] My last writeup "Microsoft Windows usp10.dll "GetFontDesc()" Integer Underflow Vulnerability": http://blogs.flexerasoftware.com/vulnerability-management/2015/12/vulnerability-in-microsofts-unicode-scripts-processor-allows-execution-of-arbitrary-code.html
" Microsoft Windows usp10.dll GetFontDesc() 整数溢出漏洞(CVE-2015-6130),来自 2015 年底的一篇 Blog: https://t.co/MhMoFh8kEx"
-

[ Windows ] Jason Shirk on "PowerShell Engine Enhancements" https://msdn.microsoft.com/en-us/powershell/wmf/5.1/features-scenarios-cache/ps-engine-enhancements
" PowerShell 引擎 5.1 版本的一些变化: https://t.co/VQ1e21Y8dU "
-

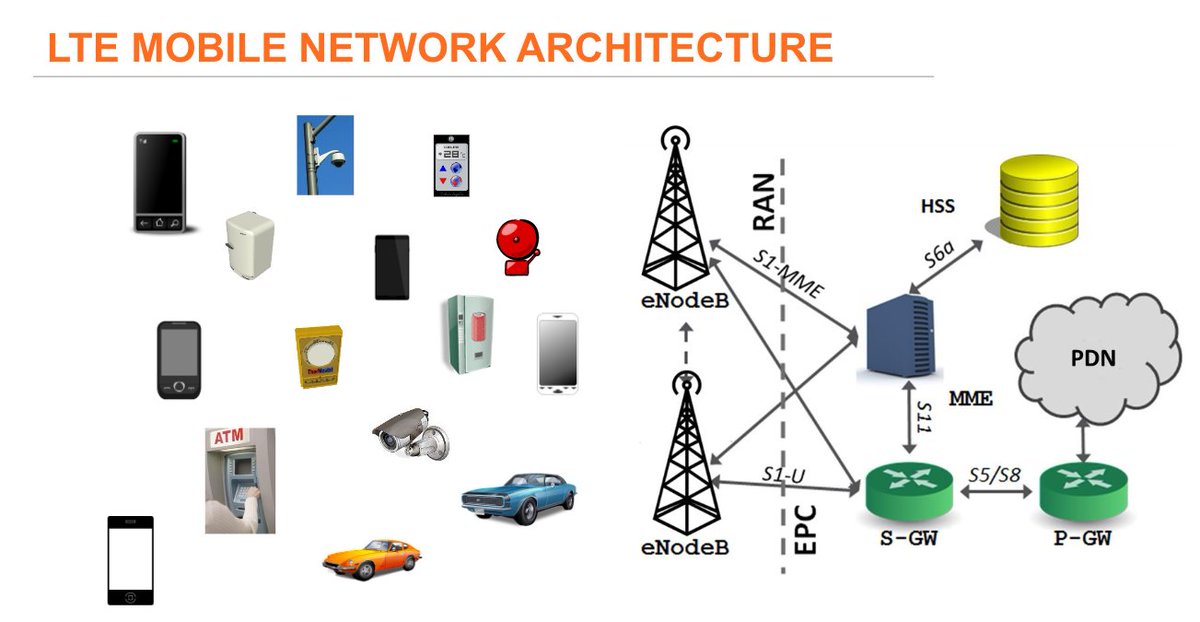
[ WirelessSecurity ] LTE MOBILITY SECURITY AND VIRTUALIZATION [PDF] http://www.ee.columbia.edu/~roger/LTE_security_tutorial_ICC_May_2016.pdf #LTE #SDR https://t.co/xXmCcuuORJ
"LTE 移动安全与虚拟化: https://t.co/U4gJy6OCmP "
-

[ WirelessSecurity ] srsUE:Open source software radio 3GPP LTE UE https://github.com/srslte/srsue #bladeRF #SDR #LTE
"srsUE - 一套开源的 3GPP LTE 用户设备实现: https://t.co/eKfDgDwtpn "
-

[ WirelessSecurity ] MANA Toolkit – Rogue Access Point (evilAP) And MiTM Attack Tool http://www.darknet.org.uk/2016/09/mana-toolkit-rogue-access-point-evilap-mitm-attack-tool/
"MANA Toolkit — WiFi AP 欺骗和中间人攻击工具: https://t.co/L8McESqYzv"
-

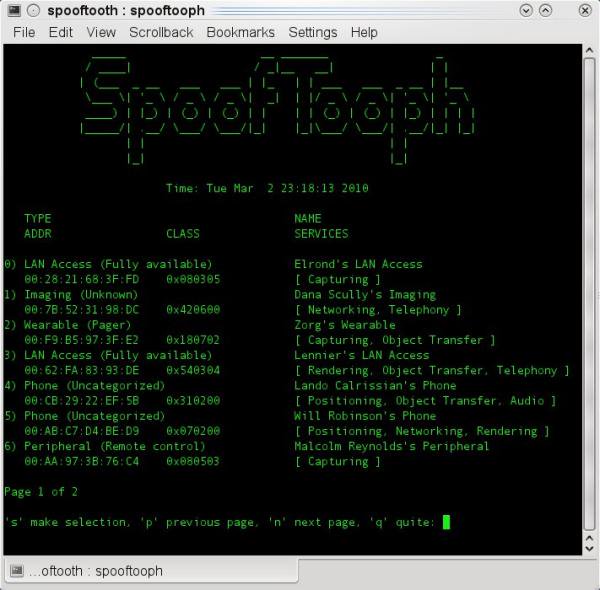
[ WirelessSecurity ] Spooftooph - Automated Tool for Spoofing or Cloning Bluetooth Device http://ethicalhackingnews.blogspot.jp/2013/02/spooftooph-automated-tool-for-spoofing.html https://t.co/kimQUvU1S1
"Spooftooph - 能够实现蓝牙设备克隆和欺骗的自动化工具: https://t.co/wg01jnxxUH "
-

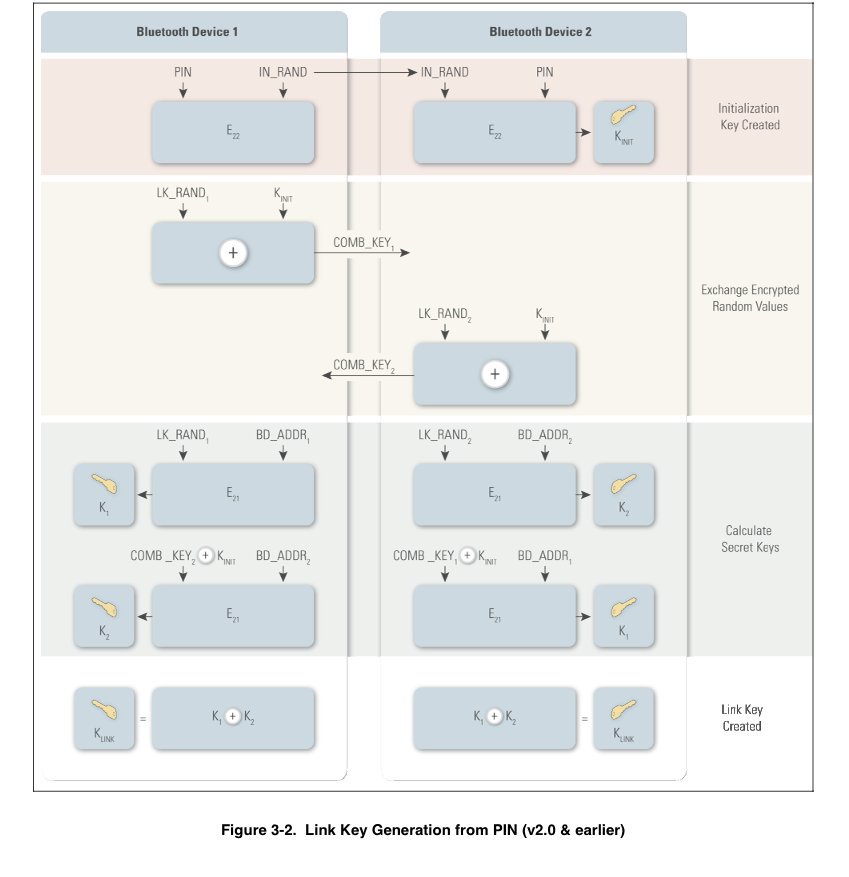
[ WirelessSecurity ] Guide to Bluetooth Security [PDF] http://large.stanford.edu/courses/2012/ph250/roth1/docs/890066.pdf #Bluetooth #Checklist #IoT https://t.co/qNzsHvCScE
"蓝牙安全研究入门指南,来自 2008 年的一篇文档: http://large.stanford.edu/courses/2012/ph250/roth1/docs/890066.pdf "
-
[ Pentest ] Windows 域横向渗透: http://www.mottoin.com/89413.html 目的是获取 redhook.DA 域的一个可用的账户,当前攻击者已在公司网络内,但并未在同一个子网
-
[ Android ] Blender: Self-randomizing Address Space Layout for Android Apps,Paper: https://loccs.sjtu.edu.cn//gossip/blog/2016/09/20/2016-09-20/ 针对 Android 5.x 版本 ASLR 机制的安全性,本文介绍了一种新的攻击方式:return-to-art (ret2art),并且针对这种方式提出了相应的解决方案

 Xuanwu Spider via MottoIN
Xuanwu Spider via MottoIN