
腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Android ] Run Android 6.0 Marshmallow on Your PC With Android-x86 6.0 : http://www.android-x86.org/releases/releasenote-6-0-r1
" 在 PC 机上的 Android x86 6.0 模拟器中运行 Android 6.0 Marshmallow 版本: https://t.co/J0dtIZbstX"
-

[ Browser ] Mozilla will patch zero-day Firefox bug to fiddle man-in-the-middle diddle http://www.theregister.co.uk/2016/09/18/mozilla_tor_flaws/ Zero Day: https://hackernoon.com/tor-browser-exposed-anti-privacy-implantation-at-mass-scale-bd68e9eb1e95#.3m17mqa45
"Mozilla Firefox 浏览器 9 月 20 号将会发布更新,修复一个中间人劫持漏洞,该漏洞影响 Tor 网络的匿名性: https://t.co/8a7B2Q2v2O 漏洞的分析: https://t.co/UPCUXQCYZg"
-

[ Crypto ] Slides from my @ strangeloop_stl talk "Frontiers in Cryptography": https://speakerdeck.com/tarcieri/frontiers-in-cryptography
" 加密方向的前沿研究: https://t.co/oFfwYirXVx"
-

[ Debug ] New version of #DbgKit 2.1 is out. Check out new Device Explorer command and new features in !mm command #WinDbg http://www.andreybazhan.com/dbgkit.html
" Windows 调试器的图形界面扩展 DbgKit 更新 2.1 版本: https://t.co/vWtnJvrYsZ 本次更新的新变化: http://www.andreybazhan.com/whats-new-in-dbgkit.txt "
-

[ iOS ] . @ heathermahalik: A glimpse of iOS 10 from a smartphone forensic perspective http://ow.ly/UDfT504AGnS
" 从智能手机取证的角度看 iOS 10: https://t.co/wqgxs81igU"
-

[ macOS ] Intercepting Passwords to Escalate Privileges on OS X is now released with source code. Enjoy. https://www.scriptjunkie.us/2016/09/intercepting-passwords-to-escalate-privileges-on-os-x/
" 劫持 OS X 的用户密码,获取特权: https://t.co/VRYYArn4Zp"
-

[ Malware ] Locky Ransomware Hides Inside Packed .DLL https://blogs.mcafee.com/mcafee-labs/locky-ransomware-hides-inside-packed-dll/
" 藏在 DLL 中的 Locky 勒索软件,来自 McAfee Blog: https://t.co/KSQ8X2KCBQ"
-

[ Others ] Blind Java Deserialization (Part 1 - Commons Gadgets) : https://deadcode.me/blog/2016/09/02/Blind-Java-Deserialization-Commons-Gadgets.html , Part 2 - Exploitation : https://deadcode.me/blog/2016/09/18/Blind-Java-Deserialization-Part-II.html
" Blind Java Deserialization(反序列化)漏洞: https://t.co/Z0nXE3Zb8r 漏洞的利用: https://t.co/Q2rhmxuLUn"
-

[ Pentest ] Bypass-UAC, PowerShell framework for UAC attacks (no injecting dll's into explorer!) https://github.com/FuzzySecurity/PowerShell-Suite/tree/master/Bypass-UAC
" PowerShell-Suite 渗透框架中的一个 Bypass UAC 模块: https://t.co/pHnGbZ9gRs "
-

[ Pentest ] How To Exploit Windows machine With BeEF + Metasploit http://www.spriteking.com/archives/1385 #pentest #hacking #infosec https://t.co/aKHfigTuVB
" Kali Linux 渗透测试:Metasploit 与 Beef 联动打入企业内网: https://t.co/oP4wnR7RRz "
-

[ ReverseEngineering ] How to Reverse-Engineer PS Vita — 173210's Blog https://173210.github.io/psp2
" 如何逆向索尼 PS Vita: https://t.co/OJfVeS2DD8"
-

[ SCADA ] Hacking industrial processes with and undetectable PLC Rootkit http://securityaffairs.co/wordpress/51389/breaking-news/plc-rootkit.html
" Black Hat Europe 2016 会议上,两名黑客将会展示一款免杀 PLC Rootkit: https://t.co/JlApEQ0IJd"
-

[ Tools ] Linux debugging tools you'll love: a great zine by @ b0rk http://jvns.ca/blog/2016/09/07/new-zine-linux-debugging-tools-youll-love/
" 一款新的 Linux 调试工具 - Zine: https://t.co/5ZIQuRZfzA"
-

[ Vulnerability ] Reverse Engineering Cisco ASA for EXTRABACON Offsets http://zerosum0x0.blogspot.com/2016/09/reverse-engineering-cisco-asa-for.html
" 为方程式组织的 EXTRABACON Exploit 逆向 Cisco ASA,找到对应的偏移量,移植到新版本: https://t.co/WWcfYawevC "
-

[ Vulnerability ] Twice the Bits, Twice the Trouble: Vulnerabilities Induced by Migrating to 64-Bit Platforms https://www.tu-braunschweig.de/Medien-DB/sec/pubs/2016-ccs.pdf
" 迁移到 64 位平台引入的安全漏洞,Paper: https://t.co/RUl94D4k1p"
-

[ Web Security ] Facebook Page Takeover (0-Day Vulnerability worth 16,000$ bug bounty): http://arunsureshkumar.me/index.php/2016/09/16/facebook-page-takeover-zero-day-vulnerability/
"Facebook Page Takeover (值 16000 美刀的 0Day)︰ https://t.co/17xjNLn45R"
-

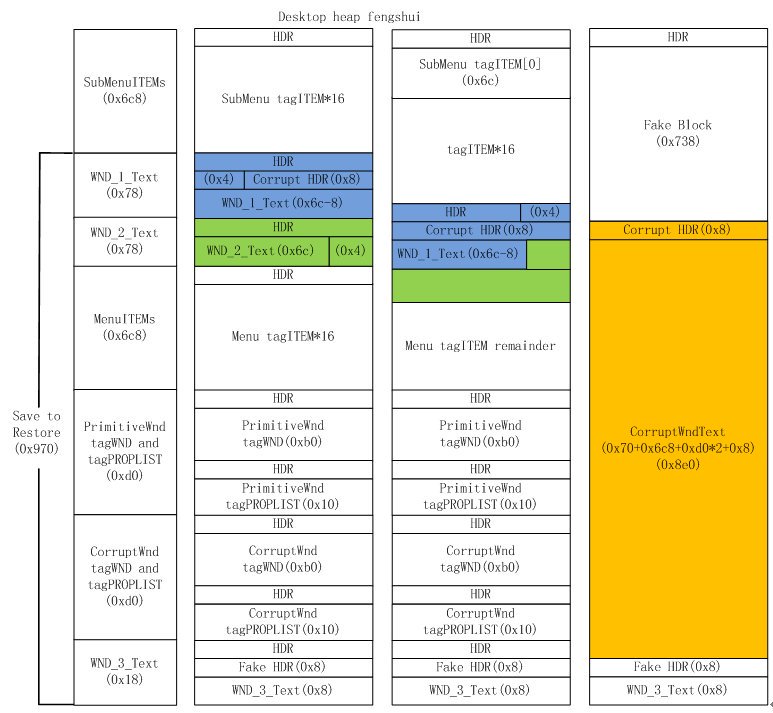
[ Windows ] Use CVE-2016-3308 corrupt win32k desktop heap. https://github.com/55-AA/CVE-2016-3308 @ zeroSteiner @ FidgetingBits https://t.co/t3q6ZR8S4D
" 如何利用 win32k Desktop heap 在内核中实现稳定的任意地址读写(CVE-2016-3308): https://t.co/LON4UTXHOs "
-

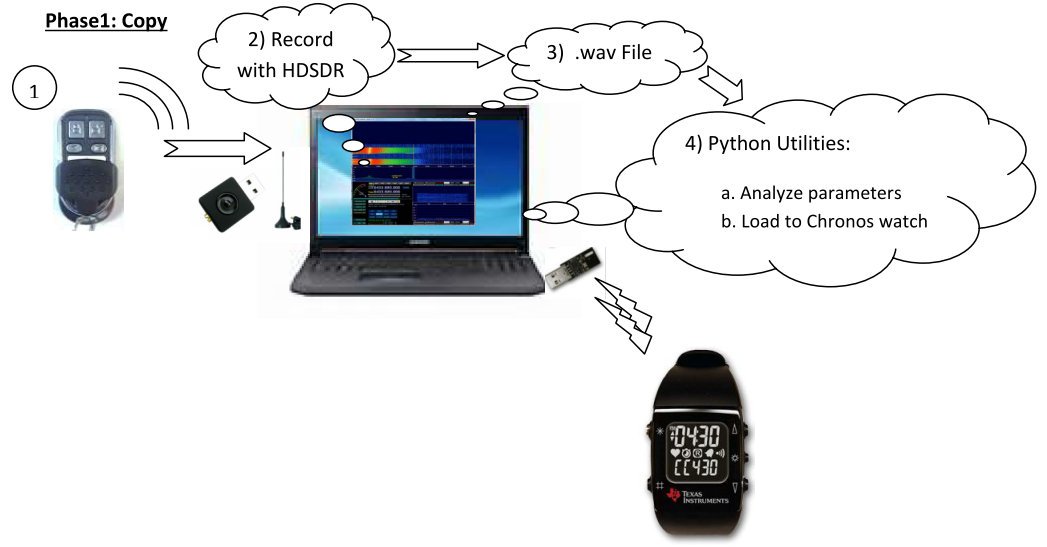
[ WirelessSecurity ] 使用 RTL-SDR 與 TI eZ430 運動手錶 ( eZ430-Chronos Watch ) 破解停車場閘門遙控器訊號 http://ruten-proteus.blogspot.jp/2014/07/rtl-sdr-ti-ez430-chronos-watch.html #SDR https://t.co/ueAjltB7aG
"使用 RTL-SDR 与 TI 的 eZ430 运动手表(EZ430-Chronos 手表)破解停车场闸门遥控器讯号: https://t.co/42mNKsd45E "
-
[ Browser ] Chromium 扩展(Extension)的页面(Page)加载过程分析 : http://blog.csdn.net/luoshengyang/article/details/52420761
-
[ Android ] Android 第三方库检测及其在安全方面的应用 : https://loccs.sjtu.edu.cn//gossip/blog/2016/09/18/2016-09-18/
 Xuanwu Spider via 看雪论坛
Xuanwu Spider via 看雪论坛