腾讯玄武实验室安全动态推送
Tencent Xuanwu Lab Security Daily News
-

[ Crypto ] dingo : A caching DNS proxy for the Google DNS over HTTPS : https://github.com/pforemski/dingo
" dingo - 一个缓存 DNS 代理。可以帮你加密所有的 DNS 流量︰ https://t.co/EnARlkHNqT"
-

[ Detect ] Approximating Attack Surfaces with Stack Traces https://www.microsoft.com/en-us/research/wp-content/uploads/2015/05/Aproximating-Attack-Surfaces-with-Stack-Traces.pdf
" 从栈回溯信息中识别攻击界面,来自微软 2015 年公开的一篇 Paper: https://t.co/roVgiZQF70 "
-

[ Others ] I had fun investigating a compiler bug that touched on some obscure CPU behaviors - details are here: https://randomascii.wordpress.com/2016/09/16/everything-old-is-new-again-and-a-compiler-bug/
" Visual Studio 编译器代码生成相关的一个 Bug ︰ https://t.co/5k6tcv1RpL"
-

[ Pentest ] PowerMemory : Exploit the credentials present in files and memory : https://github.com/giMini/PowerMemory
"PowerMemory - 攻击内存和文件中保存的凭据信息︰ https://t.co/0lYg1m47Kk"
-

[ Tools ] Config And Payload Extraction for Cuckoo Sandbox https://github.com/ctxis/CAPE
" CAPE -在 Cuckoo Sandbox 环境中配置和提取 Payload 的扩展: https://t.co/0CI449xLyD "
-

[ Vulnerability ] Hunting For Vulnerabilities in Signal - Part 1 - Attachments MAC bypass https://pwnaccelerator.github.io/2016/signal-part1.html
" 2016Blackhat演讲中Hunting For Vulnerabilities in Signal 讲解 - Part 1: https://t.co/wkiRZZHsDO"
-

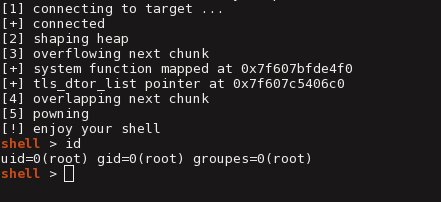
[ Vulnerability ] New excellent article by @ abu_y0ussef "The macabre dance of memory chunks" https://thisissecurity.net/2016/09/16/the-macabre-dance-of-memory-chunks/ #exploit https://t.co/nBv0EhfUiV
" 通过破坏 Memory Chunks size 实现堆溢出漏洞利用的文章: https://thisissecurity.net/2016/09/16/the-macabre-dance-of-memory-chunks/ "
-

[ Windows ] Basic Windows Privilege Escalation http://thel3l.me/blog/winprivesc/index.html
" Windows 提权方法总结: https://t.co/auaZDQjBbA"
-

[ WirelessSecurity ] New blogpost - Piotr Osuch on using H-field Electromagnetic analysis to capture data transmitted over serial https://labs.mwrinfosecurity.com/blog/h-field-electromagnetic-sniffing/
" H-field 电磁 Sniffer,来自 MWR Labs: https://t.co/DpBpZNbAcK"